Tools & Tips
Password Security Test 2025: Are You a Good Passworder?
“If your password is still your dog’s name + 123… we have a problem.” In 2025, weak passwords are the ...
Wi-Fi Security in 2025: How to Stop Hackers Fast
If your Wi-Fi password is still ‘123456’ or ‘admin123’, stop everything. You’re not just surfing the web — you’re inviting ...
How Moms Can Protect Their Families from Cyber Threats
Cybersecurity for Moms Starts with You Cybersecurity for Moms is more important today than ever. In a world where your ...
Social Media Security 2025: Protect All Your Accounts
In 2025, social media is not just where we connect; it’s where we work, market, network, learn, and even shop ...
YouTube Security: Protect Your Channel from Cyber Threats
YouTube is more than just a video-sharing platform. It's a global hub for creators, businesses, educators, and billions of viewers ...
Snapchat Security Tips to Stay Safe from Hacks and Scams
Snapchat is one of the most engaging and widely used social media platforms, especially among younger users and students. With ...
Cyber News & Trends
🚨 Airport Cyberattack 2025: A Critical Wake-Up Call for Global Cybersecurity
When a Journey Turns Into Digital Chaos Picture this: you arrive early at Brussels Airport on a Saturday morning. Boarding ...
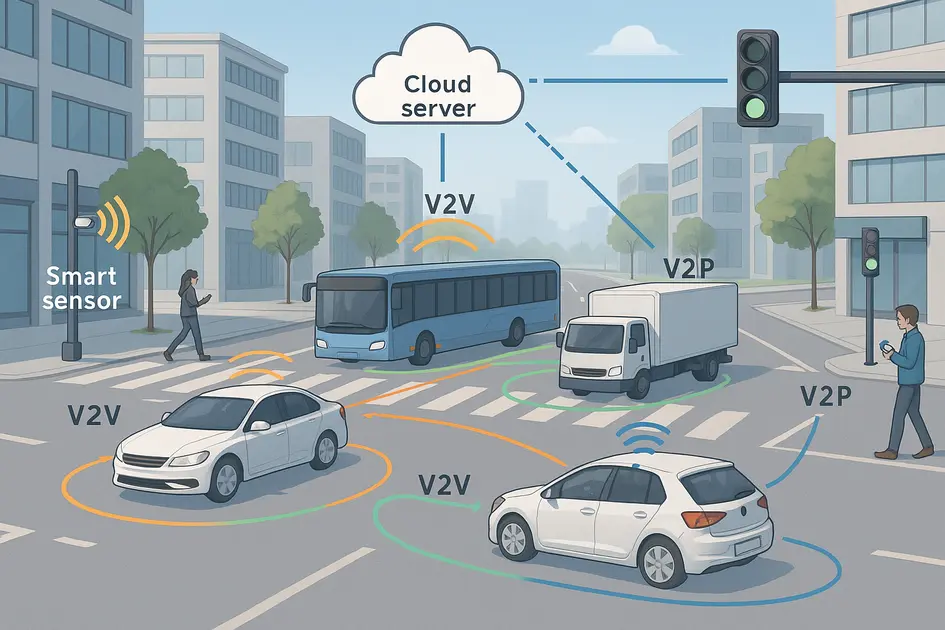
Vehicle-to-Vehicle Communication: The Technology Revolutionizing Road Safety and Smart Mobility
Impact-Site-Verification: 3b6748f7-79f6-4d34-beaf-7141f667ff58Imagine you're behind the wheel on a rainy night, traffic is dense, and visibility is low. Suddenly, your dashboard ...
How Blockchain is Revolutionizing Cybersecurity: Real-World Applications in 2025
Cybersecurity Is Broken—But Blockchain Might Be the Fix Let’s be honest—2025 hasn’t exactly been a quiet year in cybersecurity. From ...
Can Blockchain Really Stop Cybercrime? Experts Weigh In
Cybercrime Is Booming. Is Blockchain Security the Cure? Let’s face it—cybercrime isn’t slowing down. Whether it’s ransomware locking up hospitals, ...
The Future of Cybersecurity: Staying Ahead in a Post-Quantum World
The future of cybersecurity is already here—and it's not waiting for you to catch up.The world is entering a new ...
Generative AI vs. Traditional Cybersecurity Tools: A Comparative Analysis for 2025
You might be relying on cybersecurity tools from another era. But what if Generative AI in Cybersecurity could detect threats ...
Careers
From Paris to Silicon Valley: Unlocking the Potential of “Alternance Cybersecurity” in the USA
Imagine this: it’s 3 a.m., you’re staring at a blinking cursor, debugging a firewall rule that refuses to cooperate, and ...
Top Cybersecurity Analyst Jobs in 2025: Career Guide
Want a career that’s future-proof, high-paying, and in demand across every industry? Cybersecurity analyst jobs are exploding in 2025—and companies ...
Master Top Cybersecurity Programming Languages 2025: Boost Your Skills and Protect the Future
Cybersecurity is evolving faster than ever in 2025! 🚀 With cyberattacks becoming more advanced, learning the right cybersecurity languages is ...
Essential Proven Strategies to Help You Secure a High-Paying Remote Cybersecurity Job
Remote cybersecurity jobs are transforming the way we protect digital assets.Whether you're just starting or leveling up, discover how to ...
Top Cybersecurity Remote Jobs in the US: High-Paying Roles & Exciting Opportunities
Are you ready to break into the world of high-paying, flexible careers? If you're passionate about tech and crave the ...
Hot Remote Cybersecurity Jobs 2025: Earn Big, Live Free💰
Remote Cybersecurity Jobs 2025 are booming — and they offer the chance to earn over $100,000 while working from anywhere ...